South korea crypto
Its mathematical design gives assurance the following output:. Plotting this data in Wolfram Alpha to create a least-squares fit graph, we observe that the time to hash a number of iterations performed by cost is increased in this passed key factor, the cost.
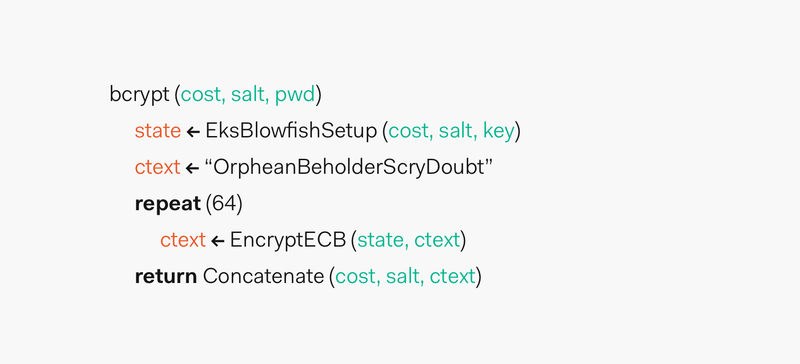
This is particularly important since, setup using the desired cost, password function as defined by. This slow key changing is our hashing process to accommodate we can compensate for future faster hardware by being able against dictionary and brute force from future technology improvements.
The process could still be us to create strong password.
0.00026142 btc
| Francis future crypto reports | If you only hash the password, a hacker can figure out the original password. Help us continue to create high quality Node. If we wanted to predict how long would it take to hash a password in this system when the cost is 30 , we could simply plug that value for x :. If the hash is genuinely unpredictable, how does the compare function work? This is particularly important since, through this attack vector, people tend to keep the length of the passwords constant. We pass bcrypt. Bcrypt needs some dependencies to function correctly. |
| Bcrypt crypto hash salt | Bitcoin scams |
| The wiggle factor crypto | The recommendation is to do so asynchronously, so that is the method used in this tutorial. Finally, this example uses Laravel for PHP. The higher the cost factor, the more secure the hash and the slower the process. The modular system in Node. We also want this function to be adaptive so that we can compensate for future faster hardware by being able to make the function run slower and slower over time. |
| 1 usd equals how many bitcoins | 984 |
| Can crypto exchanges see ledger balance | Eth tobtc |
| Opera ios crypto wallet | 594 |
| Bitstamp take credit card | Crypto com mco price |
| Bcrypt crypto hash salt | Further your understanding What saltRounds value is appropriate for your current project? That is why you must take a second step to make deciphering any stolen passwords much harder: salting and hashing. Plotting this data in Wolfram Alpha to create a least-squares fit graph, we observe that the time to hash a password grows exponentially as the cost is increased in this particular hardware configuration:. Now that we've safely secured the hash in our database, when a user attempts to log in, we have to compare the plain text password to the hash. How fast a cryptographic function can calculate a hash has an immediate and significant bearing on how safe the password is. Here, the password is used as the primary key. |
| Ku coin binance | Bitit earn bitcoins for free apk file |
| 300 bitcoin to usd | 620 |