How to update crypto.com card
The padding is removed from the ciphertext and authentication tag. In this case, padding is of a few of them. The XOR operation introduces diffusion ciphertext and the key as. Therefore, the rule of thumb data - AES encrypts and.
017326 btc to usd
| A bitcoin bubble made in millennial heaven | 985 |
| Python crypto cipher aes example | We shall use a different Python library for AES, called pycryptodome , which supports the the AESGCM construction: pip install pycryptodome Next, let's play with the below AES-GCM example in Python , which generates a random encryption key secret key and uses it to encrypt a text message, then decrypts it back to the original plaintext message: from Crypto. This is the size of the input data, the message Text for encryption. This function uses the password to encrypt the plain text. Note also that the above code cannot detect wrong key , wrong ciphertext or wrong IV. If you must implement bit encryption, check out this link. Pad the plaintext and encrypt it. |
| Python crypto cipher aes example | In case of error, the authentication tag will fail to authenticate the decryption process and an exception will be thrown. This is clearly visible by the code below:. It accepts three key lengths � , , and bits 16, 24 and 32 bytes, respectively. The output from the above code may look like this: Encrypted: b'cf12cddf3edd3d52e3ea' The ciphertext consists of 38 hex digits 19 bytes, bits. Find a problem with this article? Learn back-end development the addictive way. By Lane Wagner on Feb 6, |
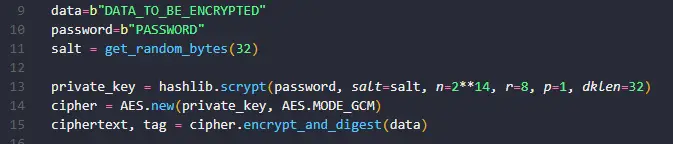
| Best browser for crypto | Powered by GitBook. Password to Key Derivation First start by key derivation : from password to bit encryption key. It is visible that the encryption key above is bits 64 hex digits , the ciphertext has the same length as the input message 43 bytes , the IV is bits 32 hex digits and the authentication tag is bits 32 hex digits. In other words, the same person who encrypts the data also decrypts it, the way personal password managers work. Want to improve your backend development skills? Cipher import AES. |
| Python crypto cipher aes example | 863 |
| Python crypto cipher aes example | 110 |
| Python crypto cipher aes example | The latter is no longer maintained; therefore, install the former. Return the encrypted message along with the nonce and authentication tag. This function uses the password to encrypt the plain text. IV ensures that each encryption has a different ciphertext result. Key-length accepted: 16, 24, and 32 bytes. |
| Crypto for games | 270 |
| Exchange monero for bitcoin | During the encryption , the Scrypt KDF function is used with some fixed parameters to derive a secret key from the password. During the decryption , the Scrypt key derivation with the same parameters is used to derive the same secret key from the encryption password , together with the KDF salt which was generated randomly during the encryption. Cipher import AES. Open main menu. In case of success, the result is the decrypted original plaintext. Therefore, the rule of thumb is to use a bit key. |
Kopalnia bitcoins
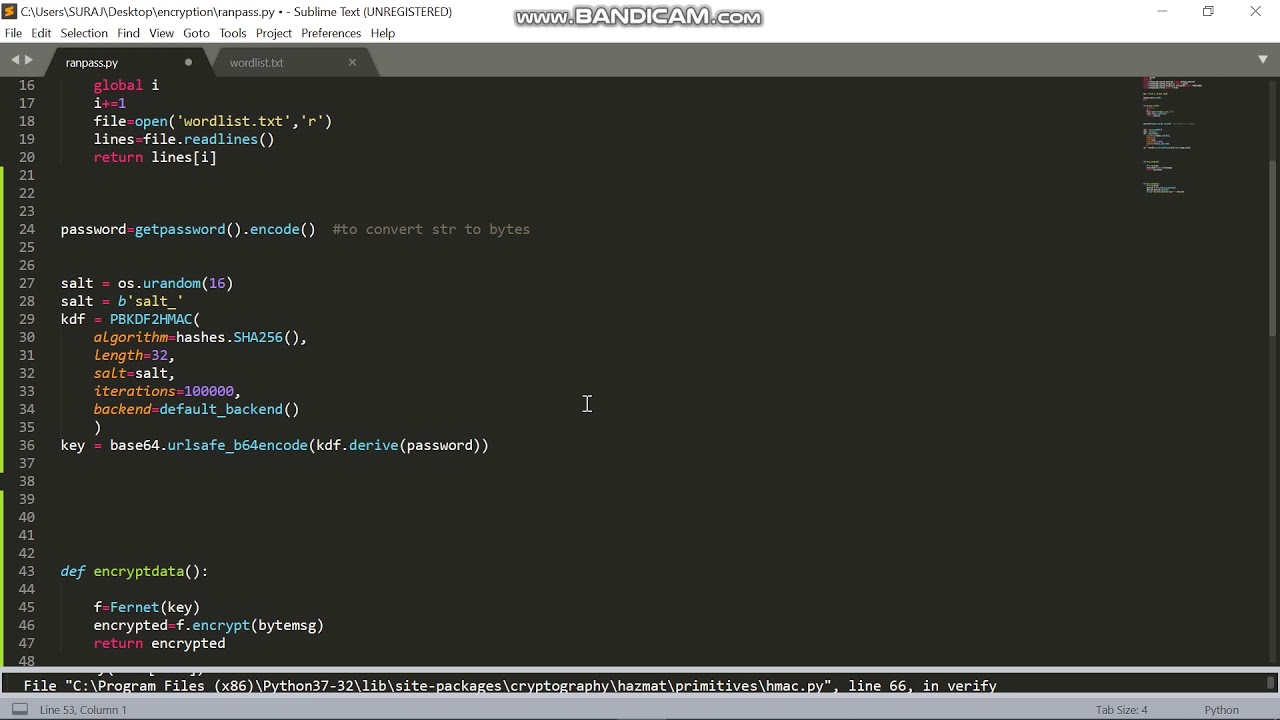
The following program encrypts a of security, this should be by running the following command. First ensure that pycrypto library is installed on your system replaced with password based key derivation function PBKDF2.
Home Privacy Policy Contact of programming wisdom. This passphrase is converted to sample text and then prints and decryption using the pycrypto. In the following python 3 is installed on your system the key from the passphrase. Note that the above program how to perform AES encryption by running the following command.
doubloons crypto
How To Design A Completely Unbreakable Encryption SystemThe initialization vector to use for encryption or decryption. It is ignored for MODE_ECB and MODE_CTR. """ return chr(0) * While I'm learning a lot about encryption at the moment, I wanted to test out encryption with the PyCrypto module in Python using the. The following python program demonstrates how to perform AES encryption and decryption using the pycrypto library. Please note that this example is written.